Featured
Table of Contents
- – What Is A Vpn?how Does It Work?
- – What Does Vpn Mean And Should You Use One?
- – What Is A Virtual Private Network (Vpn)? - Sec...
- – What Is A Vpn: Everything You Need To Know Ab...
- – What Does Vpn Stand For? Are You Using Vpn? Y...
- – What You Need To Know About Vpns
- – Ultimate Guide To Vpns (2022 Updated)
- – Vpn Meanings - What Does Vpn Stand For?
- – What Is A Virtual Private Network (Vpn)? - S...
- – What Is Vpn On Iphone And Why Do You Need It?
- – How To Use Vpn On Your Iphone And Ipad
- – Advantages And Disadvantages Of A Vpn
What Is A Vpn?how Does It Work?
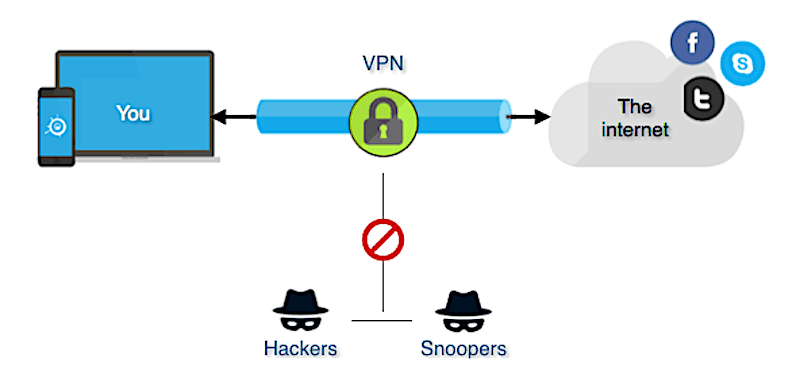
Anybody on the very same network will not be able to see what a VPN user is doing. This makes VPNs a go-to tool for online privacy.
The VPN customer is not visible to the end user unless it produces performance issues. By utilizing a VPN tunnel, a user's device will connect to another network, concealing its IP address and encrypting the data. This is what will hide private details from assailants or others hoping to access to a person's activities.
VPNs associate a user's search history with the VPN server's IP address. VPN services will have servers situated in different geographical areas, so it will look like the user might be from any one of those areas. VPNs can affect performance in numerous ways, like the speed of users' internet connections, the protocol types a VPN service provider can utilize and the type of encryption used.
What Does Vpn Mean And Should You Use One?
If the VPN connection is interfered with, the kill switch will instantly disconnect the device from the internet to eliminate the chance of IP address exposure. There are two types of kill switches: prevent devices from linking to hazardous networks when the gadget is connected to the VPN.
are more protected. They keep the device from linking to non-VPN connections even while detached from the VPN server. VPNs are utilized for virtual privacy by both regular web users and organizations. Organizations can use VPNs to make certain outdoors users that access their information center are authorized and utilizing encrypted channels.
When surfing the web, a web user might have information accessed by an assailant, including browsing practices or IP address. If privacy is a concern, a VPN can offer users with peace of mind. File encryption, privacy and the ability to navigate geographically obstructed material is what most users discover important in a VPN.
What Is A Virtual Private Network (Vpn)? - Security
The difficulties of using a VPN, nevertheless, consist of the following: Not all gadgets might support a VPN. VPNs do not secure against every danger. Paid VPNs are more trusted, secure choices. A VPN might slow down internet speeds. Privacy through VPNs has some s limitations-- for example, web browser fingerprinting can still be done.
Network administrators have several choices when it concerns deploying a VPN that consist of the following. Remote gain access to customers connect to a VPN entrance server on the organization's network. The entrance requires the gadget to validate its identity prior to approving access to internal network resources. This type typically depends on either IPsec or SSL to protect the connection.
End-node devices in the remote area do not require VPN customers since the gateway handles the connection. A lot of site-to-site VPNs linking over the internet usage IPsec. It is also typical for them to utilize carrier Multiprotocol Label Changing (MPLS) connections rather than the general public internet as the transport for site-to-site VPNs.
What Is A Vpn: Everything You Need To Know About Virtual ...

resource that talks about what vpns are
In a mobile VPN, the server still sits at the edge of the organization's network, enabling safe tunneled gain access to by verified, licensed clients. Mobile VPN tunnels are not tied to physical IP addresses, nevertheless. Rather, each tunnel is bound to a sensible IP address. That logical IP address remains to the mobile phone.
Hardware VPNs use a variety of benefits over software-based VPNs. In addition to offering improved security, hardware VPNs can supply load balancing for big customer loads. Administration is handled through a web internet browser user interface. A hardware VPN is more costly than a software-based one. Because of the expense, hardware VPNs are more feasible for larger organizations.
Paid supplier alternatives tend to be suggested more typically than totally free ones. Some VPNvendors, among lots of, consist of the following: includes a strong collection of security features with a large collection of servers. Nord, VPN has features such as Tor web browser connections for confidential web surfing, while keeping a strong stance on customer privacy.
What Does Vpn Stand For? Are You Using Vpn? You Should ...
Still, it is typically thought about a great VPN service. It has strong personal privacy and information practices focused on security and provides additional features such as split tunneling.
VPNs are legal in the United States, however users and companies must check if they are legal in particular nations. Lots of VPNs offer incredibly similar technologies, so it can be tough to choose which VPN will work best. Paid VPN services tend to be more relied on and consist of more security functions.
Around 2017, internet users in the United States found out that ISPs could gather and sell their searching history, and net neutrality ended up being an idea people needed to defend-- and successfully lost. A costs was gone by the U.S. Legislature in 2019 to bring back net neutrality, however was ultimately obstructed by the Senate.
What You Need To Know About Vpns
With this understanding, making use of VPNs ended up being a more legitimate requirement for people.
Extranet-based site-to-site In the context of site-to-site setups, the terms and are utilized to describe 2 various usage cases. An intranet site-to-site VPN explains a configuration where the websites linked by the VPN belong to the exact same organization, whereas an extranet site-to-site VPN signs up with sites coming from several organizations. Typically, people communicate with remote access VPNs, whereas companies tend to use site-to-site connections for business-to-business, cloud computing, and branch workplace scenarios.
An SSL VPN can connect from areas where IPsec encounters problem [] with Network Address Translation and firewall program rules. Datagram Transport Layer Security (DTLS) used in Cisco Any, Link VPN and in Open, Connect VPN to fix the concerns TLS has with tunneling over TCP (SSL/TLS are TCP-based, and tunneling TCP over TCP can lead to huge hold-ups and connection terminates).
Ultimate Guide To Vpns (2022 Updated)
Multiprotocol Label Switching (MPLS) functionality blurs the L2-L3 identity. [] 4026 generalized the following terms to cover L2 MPLS VPNs and L3 (BGP) VPNs, but they were presented in 2547. Client (C) gadgets A gadget that is within a customer's network and not directly connected to the provider's network. C devices are not familiar with the VPN.
Often it is simply a demarcation point between supplier and customer obligation. Other suppliers enable clients to configure it. Company edge device (PE) A device, or set of devices, at the edge of the provider network that links to customer networks through CE gadgets and provides the provider's view of the consumer website.
Company gadget (P) A gadget that runs inside the company's core network and does not directly user interface to any client endpoint. It might, for instance, offer routing for numerous provider-operated tunnels that come from different consumers' PPVPNs. While the P gadget is a key part of executing PPVPNs, it is not itself VPN-aware and does not keep VPN state.
Vpn Meanings - What Does Vpn Stand For?
From a user perspective, a VPLS makes it possible to adjoin numerous LAN sectors over a packet-switched, or optical, company core, a core transparent to the user, making the remote LAN sectors behave as one single LAN.
PW resembles VPLS, but it can offer different L2 procedures at both ends. Normally, its interface is a WAN procedure such as Asynchronous Transfer Mode or Frame Relay. In contrast, when aiming to provide the look of a LAN adjoining in between 2 or more locations, the Virtual Private LAN service or IPLS would be proper.
This section talks about the primary architectures for PPVPNs, one where the PE disambiguates duplicate addresses in a single routing instance, and the other, virtual router, in which the PE consists of a virtual router instance per VPN. The former technique, and its versions, have gained the most attention. One of the difficulties of PPVPNs includes different clients using the exact same address space, particularly the IPv4 private address area.
What Is A Virtual Private Network (Vpn)? - Security
A VPN does not make one's Web "personal". A VPN can log the user's traffic, however this depends on the VPN supplier. A VPN does not make the user immune to hackers.
Before we dive straight into the inner workings of a VPN, it is a great concept to familiarize yourself with the basics of what a VPN is and what it does. The acronym VPN means Virtual Private Network. As the name suggests, it offers users with a virtual network that is personal so that they can connect to the web in a way that is safe and protected.
We highly advise you read this article for a more thorough explanation of a what a VPN is before you read this one, but here's a brief guide in any case. However how exactly does a VPN do that? A VPN works by routing your gadget's web connection through your selected VPN's private server rather than your internet service supplier (ISP) so that when your information is transmitted to the web, it comes from the VPN instead of your computer.
What Is Vpn On Iphone And Why Do You Need It?
This implies that your information is changed into an unreadable code as it takes a trip in between your computer system and the server of the VPN.Your device is now viewed as being on the very same local network as your VPN. Your IP address will actually be the IP address of one of your VPN Company's servers.
It uses an application that develops an encrypted connection to the private network that you can then utilize to connect to the web at large. Some VPNs work as a web browser add-on. There are a myriad of add-ons you can install to web browsers like Google Chrome or Firefox, while Opera includes an integrated VPN.
This is perfect if you have several gadgets you wish to secure as it will secure every device connected to the router, conserving you having to set up the VPN separately. You'll only require to sign in when; your router will always be connected to your VPN.Connecting your router to a VPN isn't as challenging as you may think.
How To Use Vpn On Your Iphone And Ipad
The most convenient kind of router to get is one that is developed to support VPNs right now, without you needing to do anything more technical that entering your VPN information. These routers can be a little more costly than routine routers, but the benefit deserves it. Organizations typically utilize a remote-access VPN for employees who work remotely.
This is a custom-created solution that requires individualized advancement and heavy IT resources. So we've gone over how a VPN works and some different methods to execute a VPN, however why exactly should you use a VPN? The majority of people will most likely agree that the basic tenets of a VPN are a good idea.
That stated, lots of people delay getting a VPN, considering it inessential or, worse, unneeded. A great way of illustrating the requirement of a VPN is to show simply how exposed you are when your web connection is not encrypted.
Advantages And Disadvantages Of A Vpn
By not using a VPN, you're not quite screaming your most sensitive information from the rooftops, but it is a little like leaving your front door open with your personal information easily set out on a table right inside the door. Maybe you have good, honest neighbors that won't can be found in and take what is important.
Table of Contents
- – What Is A Vpn?how Does It Work?
- – What Does Vpn Mean And Should You Use One?
- – What Is A Virtual Private Network (Vpn)? - Sec...
- – What Is A Vpn: Everything You Need To Know Ab...
- – What Does Vpn Stand For? Are You Using Vpn? Y...
- – What You Need To Know About Vpns
- – Ultimate Guide To Vpns (2022 Updated)
- – Vpn Meanings - What Does Vpn Stand For?
- – What Is A Virtual Private Network (Vpn)? - S...
- – What Is Vpn On Iphone And Why Do You Need It?
- – How To Use Vpn On Your Iphone And Ipad
- – Advantages And Disadvantages Of A Vpn
Latest Posts
10 Best Vpn Services Of 2023 - Top Vpns Rated By Experts
24 Best Vpn Services Available In 2023
Stay Safe On The Go With The Fastest Mobile Vpn
More
Latest Posts
10 Best Vpn Services Of 2023 - Top Vpns Rated By Experts
24 Best Vpn Services Available In 2023
Stay Safe On The Go With The Fastest Mobile Vpn